If you are building WordPress plugins and themes, it’s crucial to prioritize security by properly escaping data. To achieve this, developers can utilize various functions or methods. This post will explain how to ensure that your code is correctly escaped.
Embarking on a journey into the realm of web development within the WordPress ecosystem requires more than just creativity and functionality. Security stands as a cornerstone, and understanding the intricacies of data link escape is paramount to fortifying your website against potential threats. In this exploration, we delve into the significance of data escape in WordPress, unraveling the complexities and offering insights into essential functions such as esc_html(), esc_url(), and more. As we navigate through practical examples, we’ll unveil the keys to secure coding practices, ensuring that your website remains resilient in the face of evolving cyber threats.
What Is Escaping Data?
Escaping data or data link escape is a way to protect output by removing any data that could be harmful, like script tags or incorrectly formed HTML. Doing this will prevent that data from being seen or executed as code. It’s essential for secure coding in WordPress, so it should be used in all WordPress development. Luckily, WordPress provides developers with several functions or methods to help remove this unwanted data. All you need to do is learn which function to use depending on the data you’re using and where you’re using it.
Plugins and premium WordPress themes in WordPress often go the extra mile by incorporating advanced escaping techniques, providing developers with pre-built solutions that prioritize not only aesthetics and functionality but also adhere to stringent security standards. These premium offerings serve as valuable assets for developers seeking a comprehensive approach to data security while streamlining their development processes.
Escaping Functions
When using WordPress, you can use many helpful data link escape functions for the most common scenarios. It’s important to pay attention to what each function does, as some will remove HTML while others will allow it. Always use the most appropriate function for the content and context of what you want to display. Remember to escape when you echo, not before.
1. esc_html()
When incorporating variables into HTML elements, it is essential to exercise caution. Suppose we want to display an item’s title taken from a database in a heading tag. In that case, we must avoid including a closing heading tag within the title. This is because such an action would break the HTML markup of the page. To prevent this issue, we can use the esc_html() function, which escapes any HTML that may exist in the title. By doing so, the function guarantees that any HTML present in the title is escaped, preventing it from being treated as HTML. As a result, the layout of the page remains intact.
2. Esc_url
When we intend to use a variable as a URL, it’s crucial to ensure that it’s safe and free of any harmful data that could lead to security breaches. To achieve this, we can utilize the “esc_url()” function, which guarantees that the output is proper and reliable for use in various contexts, such as the “src” attribute of an image or the “href” part of a link. By using this function, we can rest assured that the URL is appropriately escaped and protected from any unsafe data that could compromise our website’s security.
3. esc_js()
Sometimes, we need to include dynamic JavaScript code in a variable that may change based on different factors. However, when we intend to directly display this JavaScript code on a web page, it’s crucial to ensure proper escaping to prevent unintended code execution or security vulnerabilities. The WordPress data link escape function called “esc_js()” proves handy in this scenario. It facilitates the escape of the JavaScript code before being output to the page. Here’s a straightforward example illustrating how to use the function.
4. wp_kses()
If you want to add content to an HTML element that allows certain HTML tags, you can use the wp_kses() function. It prevents problems like script injection by allowing only safe HTML. You need three things to use it: the content you want to escape, an array of allowed HTML tags, and an array of allowed protocols. You don’t need to worry too much about this though, because there are some other functions available that do the work for you, like wp_kses_post(). This function applies the allowed HTML tags and protocols automatically when you add new content to a post. By using wp_kses_post(), any unsafe HTML tags will be removed from the content automatically, and only the allowed tags and protocols. It is helpful when you create a WordPress post and want to add images, paragraphs, links, and bold text.
5. esc_attr()
When displaying PHP code within attributes of an HTML element, excluding URLs, it is crucial to escape it properly to prevent security risks. To achieve this, it is recommended to use the ‘esc_attr()’ function, as it ensures that the output is safe for use in an attribute. For example, when working with classes, you can employ this function.
6. esc_textarea()
If you are entering data into a box and intend to display the saved information inside the box, use this data link escape function.
7. esc_html_e() and esc_attr_e()
WordPress provides wrapper functions to escape strings with localization functions. These functions include localization functions within them, avoiding the need for nesting.
In addition to adopting premium solutions, developers should embrace proactive measures for security assurance. Utilizing a website security checker becomes an invaluable tool in this pursuit. Regularly scanning your website for vulnerabilities and potential security gaps helps identify and address issues before they can be exploited. By combining the best practices of data escaping with premium tools and incorporating routine security checks, developers can establish a resilient foundation for their WordPress websites in the ever-changing digital environment.
Let’s provide a brief explanation and example program codes to show importance of escaping data in WordPress for security:
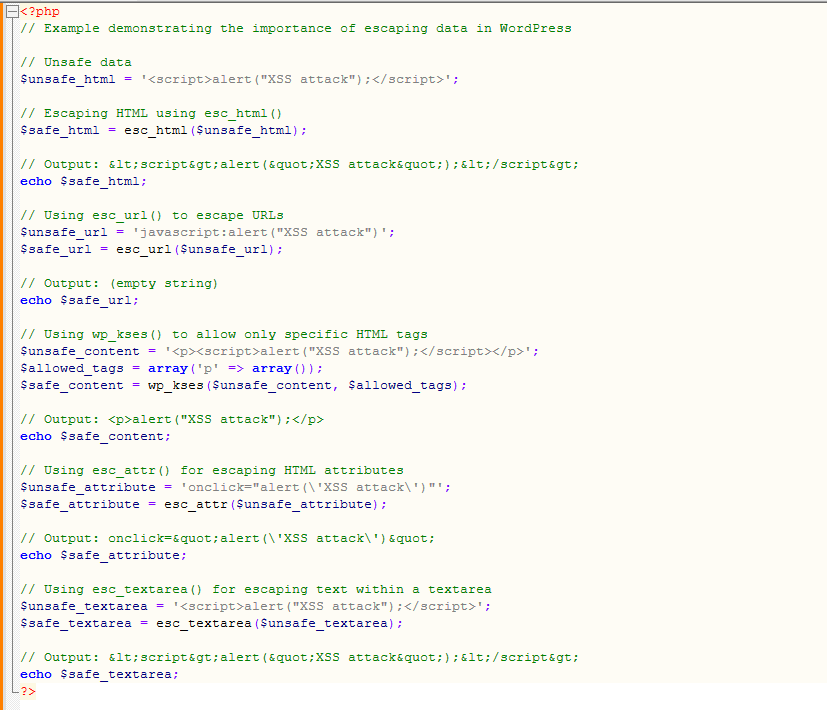
In this example, we emphasize the importance of data link escape in WordPress for security and demonstrate the use of various escaping functions depending on the context of the data being used. We use each function in a specific scenario to ensure that the output remains safe from potential security threats, such as XSS attacks.
Elaborating the Use of Each Escaping Function in the program code:
1. esc_html():
Purpose: Used to escape HTML entities in a string, making it safe for output in HTML content.
Example: $safe_html = esc_html($unsafe_html);
Explanation: This function ensures that any HTML tags or special characters in $unsafe_html are converted to their respective HTML entities. It helps prevent Cross-Site Scripting (XSS) attacks by rendering any potentially harmful code inert.
2. esc_url():
Purpose: Used to sanitize and escape URLs to prevent security vulnerabilities.
Example: $safe_url = esc_url($unsafe_url);
Explanation: This data link escape function checks and cleans the provided URL. This ensure its safety for use in the context of a link. In the example, the function sanitizes the unsafe JavaScript URL. It result in an empty string, thereby helping prevent malicious code execution.
3. wp_kses():
Purpose: Used for sanitizing and allowing only specific HTML tags in a given content.
Example: $safe_content = wp_kses($unsafe_content, $allowed_tags);
Explanation: In the example, wp_kses() is used to allow only the ‘p’ tag while removing any other potentially harmful tags. This is useful when you want to allow some HTML content but restrict certain tags to prevent security issues.
4. esc_attr():
Purpose: Used to escape HTML attributes, ensuring they are safe for use in HTML tags.
Example: $safe_attribute = esc_attr($unsafe_attribute);
Explanation: This function escapes special characters within the HTML attribute value, making it safe for insertion into HTML markup. In the example, the onclick attribute is sanitized to prevent potential code injection.
5. esc_textarea():
Purpose: Used to escape text for use within a textarea HTML element.
Example: $safe_textarea = esc_textarea($unsafe_textarea);
Explanation: This function is specifically designed for content within a textarea. It escapes special characters to prevent unwanted behavior or code execution within the textarea. In the example, it ensures that any script tags are rendered inert.
Each data link escape function serves a specific purpose in securing data output in different contexts. Such as HTML content, URLs, HTML attributes, and text area content. Using the appropriate escaping function for the specific data and context is crucial for maintaining the security of a WordPress application.
Conclusion
Securing data is crucial in WordPress development. Proper data escaping is vital to protect against potential security threats like script injection or HTML vulnerabilities. WordPress provides various data link escape functions for specific scenarios. These include esc_html(), esc_url(), esc_js(), wp_kses(), esc_attr(), and esc_textarea(). Esc_html_e() and esc_attr_e() are wrapper functions with built-in localization capabilities. By using these functions appropriately, developers can fortify their WordPress plugins and themes against potential security vulnerabilities.
Furthermore, for those seeking a streamlined approach to secure development, exploring our WordPress Theme Bundle can be highly advantageous. This bundle offers a curated selection of themes equipped with built-in security features, providing an additional layer of protection.